
Go Phish: 11 Ways To Avoid The Bait
Don’t let employees get hooked by phishing scams. Here are 11 Key Phishing Signs to watch for in your email inbox.

Don’t let employees get hooked by phishing scams. Here are 11 Key Phishing Signs to watch for in your email inbox.

Don’t let data breaches catch you out of pocket by saving now and paying later. Invest wisely in key cybersecurity solutions to reduce risk and curb damages.

The worst IT security scams slip through email cracks—which is why today, we’re breaking down the leading email scams of 2021, and what you can do with a strong cyber-defense.
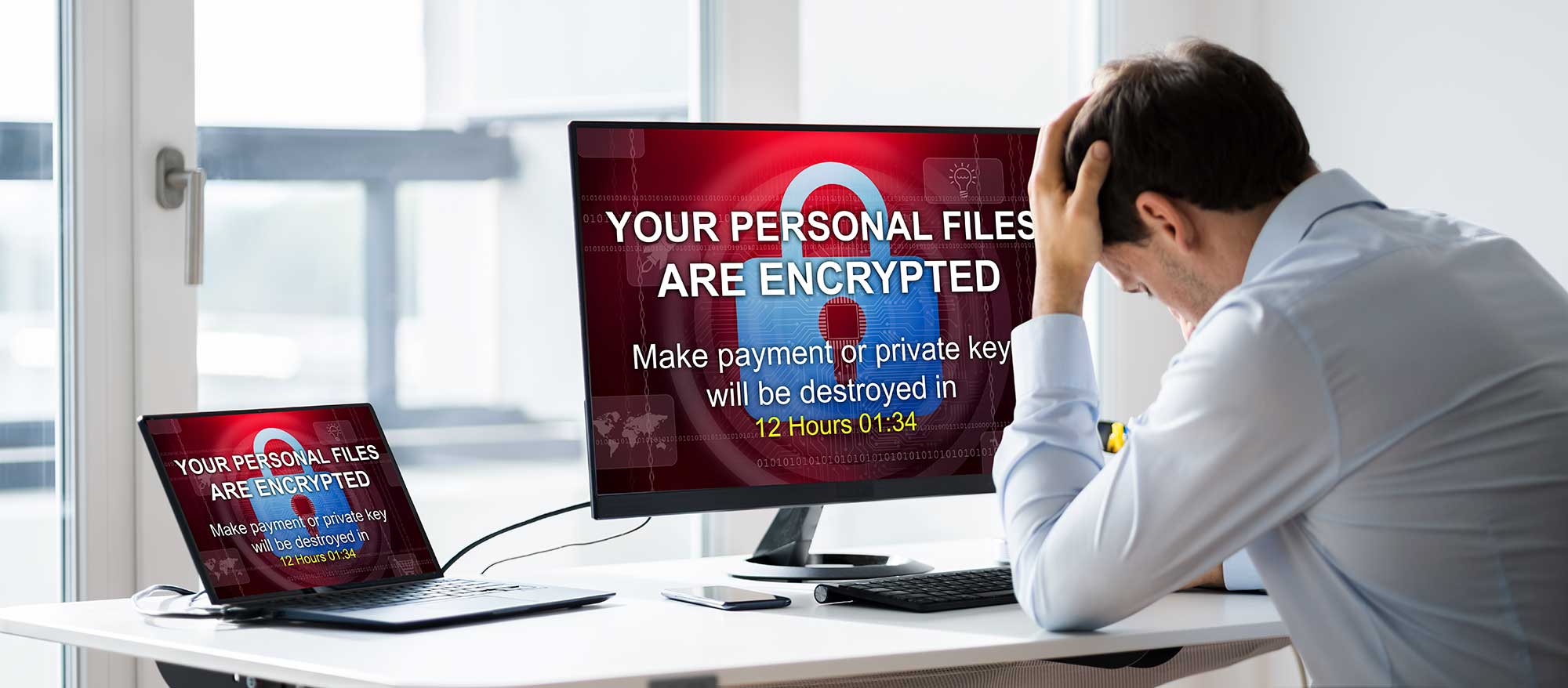
Ransomware is THE cyberthreat of 2021, and hot ticket problems demand dynamic solutions. We take a step (or six) into the world of preventative IT security.

As post-pandemic life comes into view, healthcare looks to the future with telemedicine. Here’s a quick glance at expanding horizons for digital patient care & IT security.

With cyberattacks rising an alarming 600% in the past year, an Incident Response Plan acknowledges inevitability, while taking charge of reducing the impact of negative events. Here’s where to begin and what to include.

The blank slate of your next RFP can be daunting. Whether formal submissions or just reviewing proposals as they come, here’s what to ask about as you vet vendors for your next IT security assessment.

After a year-plus on our cyber-heels, what did we all learn? Here are 4 takeaways to strengthen security post-COVID… because the next ‘normal’ in IT Security is ours to define.

New perspectives, workarounds, and efficiencies developed throughout the pandemic are likely here to stay —and so are elevated and complex cyber threats. That’s where IT security ears need to perk up.

While the best security defense is predicting where cybercriminals will strike next, those same cybercriminals are doing their best to strike where you’re not looking.
We’re here to discuss your upcoming IT security assessment and compliance audit needs.