An ever-expanding digital perimeter.
Vulnerable access privileges.
The ‘success’ of cybercrime.
This recipe has pushed cyber defense to shift faster than ever away from traditionally defined boundaries—both network and human. With business in the cloud, remote offices and workers, the Internet of Things (IoT), mobile and personal devices, and much more, the security landscape has exponentially grown in size and complexity.
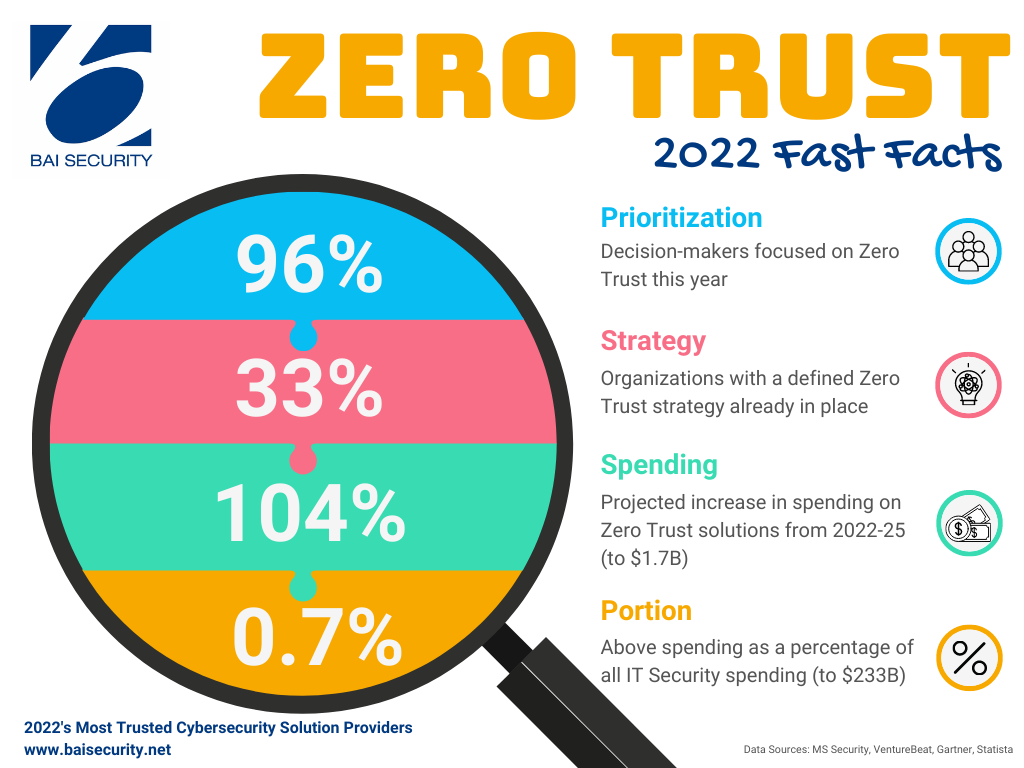
Simultaneously, aggressive hackers skillfully steal credentials, impersonate system administrators, and award themselves higher levels of access. This is why 96% of security leaders reported to Microsoft that they consider Zero Trust essential to their organizational success in 2022. However, according to Statista, only 33% of decision makers say they have a concrete strategy in place.
Zero Trust is a perspective on cybersecurity that holds everyone accountable for security regardless of role. The approach assumes there is no end or perimeter to the network in the traditional sense, nor is there any assumed trust allotted to users or assets. As NIST SP 800-207 details, Zero Trust Architecture (ZTA) prioritizes continual authentication, authorization, and validation of every user to protect resources over the network itself. In short, no one is trusted, and all digital engagement is continually validated.
Why the lack of trust? Because anyone can be compromised.
Yet as Bhagwat Swaroop, a Forbes Technology Council colleague to BAI Security’s CEO (Michael Bruck) advises, we need to think about adaptive Zero Trust for long-term resilience. As Bruck reflects, “Risk and roles change, so a dynamic strategy must have built-in responsiveness; otherwise, it’s bound to run exactly counter to its intended protections.”
Before we get into what that looks like, let’s understand a bit about how we got to this mistrusting place…
To Mistrust & Beyond
Zero Trust dates back to 2010, when Forrester analyst John Kindervag devised the term to articulate the need to secure all network access. Its recent evolution, however, has been impacted significantly and rapidly by COVID-19. According to Deloitte, 40% of organizations adopting Zero Trust have accelerated their efforts because of the pandemic.
While leaders increase their focus on validating vendors to manage third-party risk and help prevent supply chain attacks, Zero Trust is also helping to address cloud-based risk, insider threats, and hacker-targeted remote workers. Louis Columbus points to the trend for Zero Trust to serve as the foundation for hybrid cloud integrations, where legacy IT systems fused with public and private cloud platforms creates a complex landscape to defend, as SolarWinds found out the hard way, where cloud configurations lacked any least-privileged access policy.
What Government Silos Taught Us
Prior to the pandemic, the Center for Enhanced Cybersecurity at the Government Accountability Office (GAO) reported that cybersecurity was low on agencies’ list of priorities, and as a result, threat assessment was suffering to a dangerous degree.
In one instance, the GAO surveyed 26 cyberattacks on a variety of federal agencies and found that ultimately, none of the agencies could trace the attacks to their points of origin. An equally concerning amount of “intrusions” were believed to have come from inside the agencies themselves.
The problem, the GAO determined, was that the federal agencies’ cybersecurity practices were limited in scope. As opposed to the Zero Trust model, which applies to all users inside and outside of a network, there were no safety protocols in place that could protect the agencies’ systems as a whole.
In 2020, to address telework as COVID-19 swept the planet, the U.S. Navy’s top cybersecurity official admitted they took a calculated risk in allowing service members and employees to use their personal devices to conduct normal business during the pandemic—though those vulnerabilities are exactly what Zero Trust accounts for.
Now, years into a Zero Trust approach, the GAO stresses that the most common modes of attack malicious actors employ against the government are also the simplest: service members clicking on unknown hyperlinks, failing to frequently change their passwords, and ignoring network patches.
Get serious about cyber defense.
Zero Trust’s Horizons
While a 104% increase in Zero Trust solutions spending is anticipated between now and 2025 (to $1.64B), that still represents only 0.7% of overall IT Security/Risk Management spending for the same period ($233B) .
Yet compared to other cyber defense approaches, Zero Trust has a higher likelihood of stopping attacks at their source. This fact helped fuel President Biden’s 2021 executive order for ZTAs for all government entities. Guarded by a combination of tools, such as multi-factor verification and remote browser isolation, leaders are banking on this approach.
However long it takes budget priorities to reflect decision-makers’ priorities, an adaptive Zero Trust approach is key. This includes full visibility – on people in any location, devices of different generations, and via an exhaustive, objective assessment cycle that leaves no stone unturned. Gartner’s Watts and McDonald specifically recommend the foundation of your Zero Trust approach include:
- Ensure your identity management system is secure and commonly federated
- Employ adaptive access so resource access control is more detailed
- Utilize user-to-application segmentation (ZTNA, or Zero Trust Network Access)
Defining Your Organization’s Pathway
Your IT Security Assessment is a key component of calculating areas for needed security improvement.
With a dedicated force of exceptional in-house IT security experts who have worked for top-level security organizations worldwide, we employ independently validated assessment tools for comprehensive, highly accurate results.
Whether with our IT Security Assessment and Penetration Testing, our Vendor Management Risk Assessment, or any of our 10 Assessments & Best Practice Evaluations, take the next step toward adopting and adapting your Zero Trust approach—contact us today!