A good phishing scam falls into the category of fastest rising cybercrime methods worldwide. Phishing is wildly “successful” in using its victim’s everyday self against them to fuel digital chaos. Through effective social engineering, many victims are blind to the crime during and even after it’s occurred.
What’s particularly perplexing is that traits considered positive in humans are often the very ones that pave the way for victimization. In a recent study from researchers at Texas Tech University, characteristics associated with higher phishing susceptibility included curiosity, conscientiousness, and extraversion—all widely considered net positives in most societies.
But the digital world is different from ours, which means adjusting our whole selves accordingly to defend effectively. So let’s dive into the anatomy of a phishing victim and how to use knowledge of our human traits to fend off phishing attempts.
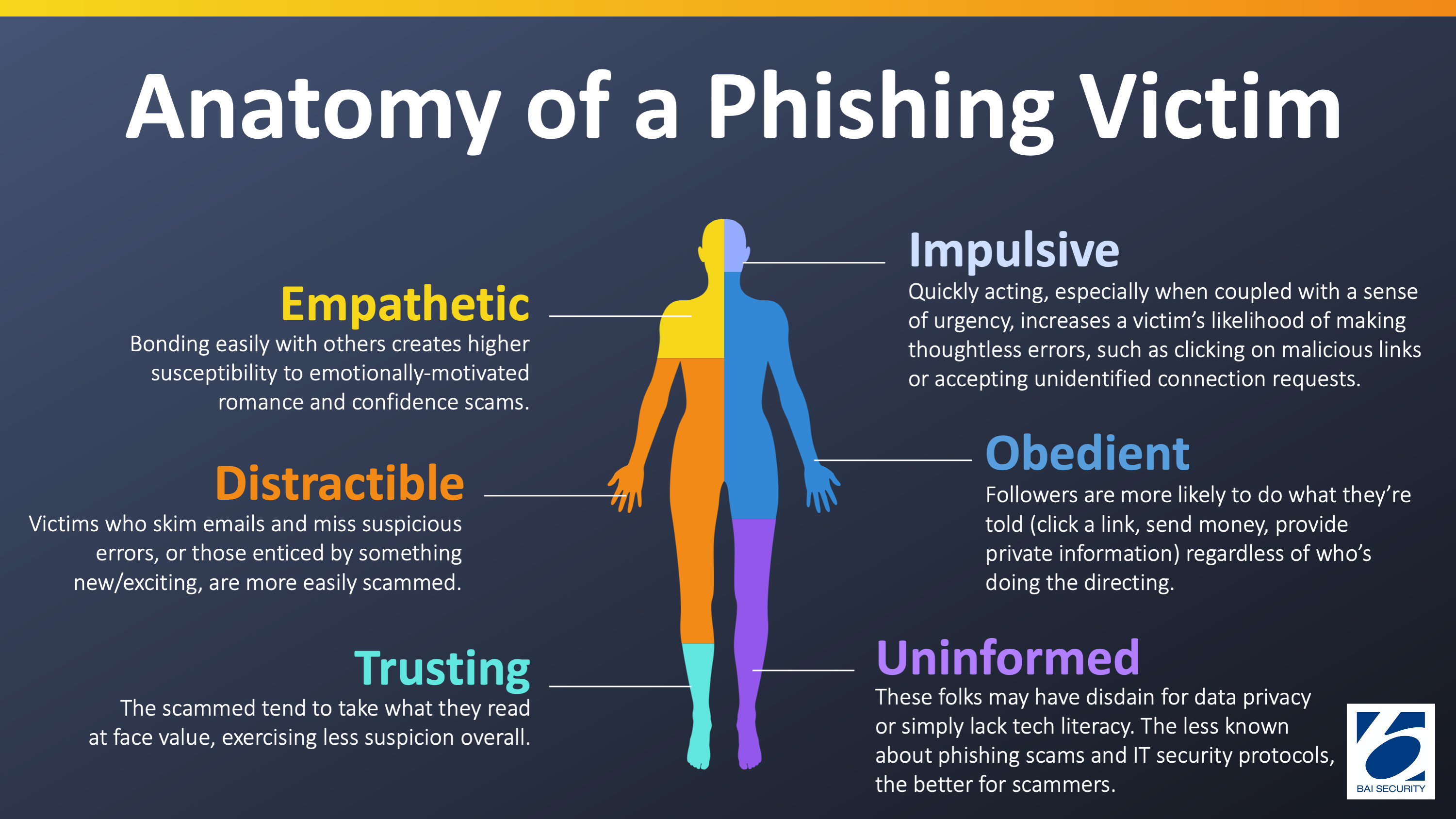
The Phishing Victim Is…
Impulsive
The Internet is hard-wired to amplify our impulsivity—the tendency to act quickly without thinking critically about our actions. Scammers rely on impulsive actors to be willing to click on foreign links in emails or accept random connection requests.
Cybersecurity expert and University of Florida Associate Professor Daniela Oliveira reminds us that “by appealing to our biases and emotions, phishing tries to get us to stay in automatic mode […] to make a fast, not a thoughtful decision.” Nobody wants to sort through a crowded inbox during a busy work day and read their emails all the way through. If you’re alerted to something like an overdrawn bank account or a credit card security breach, you’re most likely to jump into action, no questions asked.
Coupling impulsivity with urgency is the trap here, and though there’s no easy way around this one, an important coping strategy is to take your time. If something registers as strange or out of place, save it to review later. Don’t let the phisher send you through an unfamiliar link or to a sign-in page. Your cyber-safety is always worth a minute or two to validate authentic engagement.
Empathetic
The confidence/romance scams described in our recent article, 7 Rising Cybercrime Ploys & Protections, are designed to tug at victims’ heartstrings via social media-based relationships. Higher-empathy individuals are overwhelmingly quicker to develop a bond with their scammers, believe their promises of love and devotion, and ultimately be willing to transfer money when the scammers shift their crosshairs to their true target… your bank account.
As a general rule, unsolicited contact on social media should be shut down as soon as possible, unless you’re personally familiar with the person reaching out. People who offer sob stories are likely manipulating your emotions and setting you up to hand over your credit card information.
Distractible
“Easily distracted” goes hand in hand with impulsivity, which increases tenfold on the Internet. Texas Tech found that people with curious, addictive personalities were significantly more susceptible to phishing scams, specifically chasing new experiences, enticed by the promise of something new. For instance, a link in their inbox to explore meant that people reading over phishing messages were less likely to catch the key tells, like spelling and grammar mistakes or unofficial email addresses from seemingly official institutions.
The more time and focus you apply to screening your emails and critically interrogating your behavior online, the more ingrained it will become. If you’re curious about where a link from an allegedly official entity might lead, hover over the link first to confirm the URL makes sense (correct domain for the organization and logical page link). Take a moment to check their website directly to do your own research on what they’re offering you. Even read potentially suspicious emails aloud to catch errors your silent skimming may otherwise miss.
Obedient
Some people are simply driven to do what they’re told, and scammers love to take advantage. One of the more popular “hooks” in phishing is correspondence from high-profile, authoritative entities like the IRS or, more recently, the CDC.
Luckily, these entities are also aware of how frequently scammers impersonate them. Most government websites ensure the general public that they will never contact citizens unsolicited. Those websites are also handy tools to check your own status. If the IRS is claiming tax fraud, for instance, you can go to their site and reach out to an area agent. Nine times out of ten, the claim is a scammer wielding recognizable names as a scare tactic.
As a rule of thumb with messages in question, it’s wise to never make use of contact information or links embedded therein. Remember that campaigns calling for money or sensitive information are almost assuredly fraudulent; the government does not initiate personal monetary transfers, and they already have your account information on hand.
Get serious about cyber defense.
Trusting
Near to the foundation of our phishing victim is an inherent sense of trust. You want to believe that person who’s come to you for help, asking for support for a surgery or monetary relief for victims of a natural disaster. You know your mother’s family friend from college would only ask for a loan if they really needed it, right?
This all boils down to the fundamentals of online interaction: lead with zero trust. Assume that interactions coming in from the outside are looking to benefit themselves, and treat them with the appropriate caution until they can prove otherwise. Take steps to protect the privacy of your personal data above all else, because once in the hands of the wrong person, it’s a long and messy clean-up to re-establish a clean profile with various institutions.
Uninformed
A phishing victim is, first and foremost, uninformed about IT security. They may have a sense of disdain towards it or the concept of data privacy. They may simply lack technological literacy. Either way, cyber-education makes a major difference in your susceptibility to phishing scams—and the more you know, the harder it is for scammers to get anything by you.
Employers that take steps to normalize IT security culture in the workplace are already putting their employees ahead of the game. Coworkers can help each other spot suspicious correspondence and communicate more openly and immediately with their IT security team, creating a more secure and cyber-safe environment for everyone.
Embody The Solution(s)
Teaching your team to lead with caution, low trust, and even suspicion in online engagement can significantly improve your organization’s security awareness and resilience. So can an objective Social Engineering Evaluation and/or Red Team Assessment.
To evaluate the real-world effectiveness of your existing security controls and personnel against an active, skilled human attacker, call on the experts at BAI Security and contact us today!