Can you teach an old cyber-strategy new tricks? Signs point to yes—as workplaces shift gears to the digital world and attack surfaces expand, IT security tactics are playing catch-up with impressive speed.
But old habits die hard for your human workers, and cybercriminals are eager to take advantage. Social engineering, the art of exploiting people for their digital identity and security credentials, is alive and well in 2022, and leading the pack in the FBI’s recent Internet Crime Report.
BAI Security is here to help you examine key stats to help inform employee training and cyber defense priorities.
Costs Are Rising Far Faster Than Incidents
LOSSES
- $18.7B: Cybercrime losses from 2017 to 2021 filed with the Internet Crime Complaint Center (IC3).
- $6.9B: Cybercrime losses last year alone, making up 37% of losses for the past five years.
UPS & DOWNS
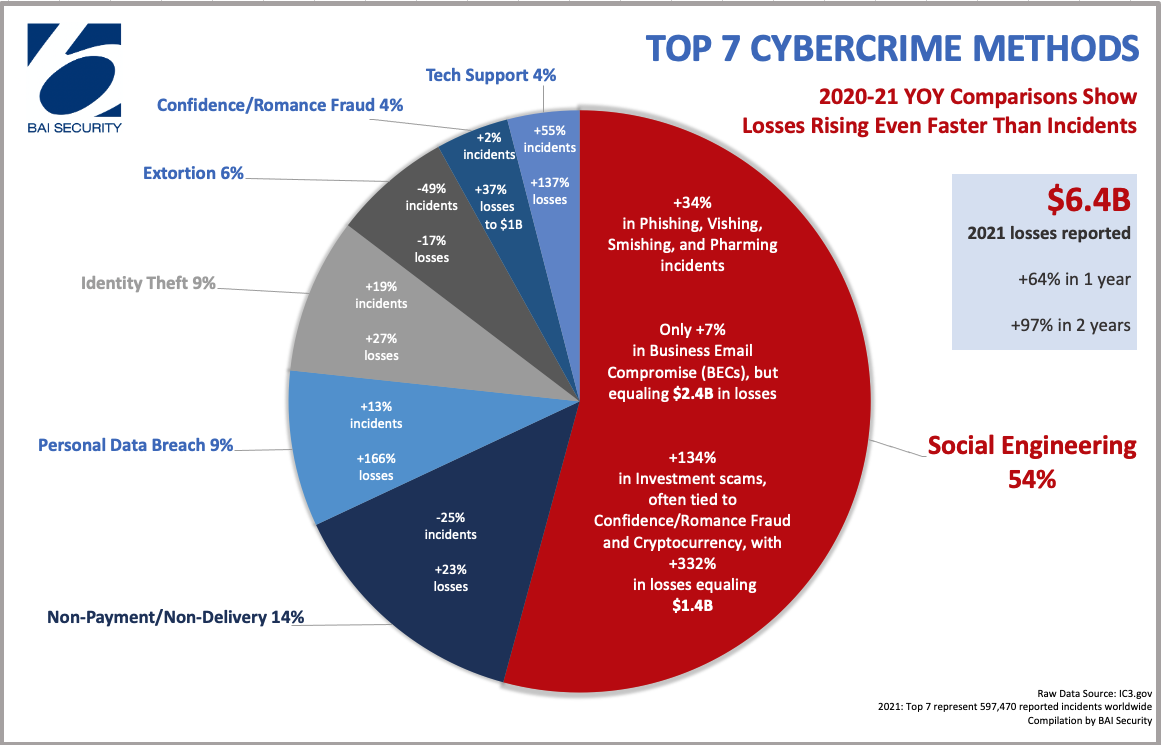
- +34% in Phishing, Vishing, Smishing, and Pharming. The two-year increase in these four prevailing scams was 182%. Business Email Compromise (BECs) alone made up nearly $2.4B of the $6.4B losses in 2021, even though they only grew 7% in incidents, while investment scams rose 134% in frequency and 332% in costs equaling $1.4B.
- – 25% in Non-Payment/Non-Delivery incidents in 2021, though losses rose 27% compared to 2020.
- +13% in Personal Data Breaches in 2021, but losses skyrocketed 166% since last year.
- +19% in Identity Theft in 2021.
- – 49% in Extortion in 2021.
- +2% in Confidence Fraud/Romance incidents in 2021; however the increase in losses jumped 37% last year alone to nearly $1B, making this the third most costly category of 2021.
- +55% in Tech Support scams, where losses jumped 137% from 2020 to 2021.
REPORTING
- +52% vs. Just +7%: The growth in reported cybercrime losses vs. the growth in complaints regarding internet scams worldwide.
Where To Begin Defending
As the data shows, social engineering is cybercriminals’ go-to, so let’s start there. Many folks have become aware of phishing (using social engineering tricks, typically by email, to get users to send money or give up coveted personal or professional data, such as bank card numbers, contact information, or login credentials. And these days, cybercriminals also use vishing (the phone version of phishing), as well as smishing (the text version of phishing).
But thanks (or no thanks) to greater security awareness of the above methods, a newer method is quickly rising.
Pharming uses the DNS cache on a user’s device or a provider’s network equipment to redirect the user from a website they intended to visit to a fraudulent one that looks identical. Once there, a user’s confidential information is up for grabs. Pharming is most often used with online banking and other ecommerce systems where money is changing electronic hands.
Pharming IS hard to detect, but you can steer clear by avoiding links and attachments from folks you don’t know, where DNS poisoning software or pharming malware may be embedded. Also, hover over links first to confirm the address to which you’re headed, and only click through on https:// addresses. Ignore overly attractive e-commerce deals, as they’re too good to be true. Lastly, use two-step authentication, a secure DNS service, updated antivirus software, and strong password settings on your home router.
Here’s more information on social engineering techniques.
Don’t Trust The Company Man
People believe what they see—which is why cybercriminals are so fond of compromising business email accounts. Last year, business email compromise (BECs) snatched up $2.4 billion via phony wire transfers, mostly credited to commandeered emails that would contact others within the company, looking as legit as a coworker, and request money be transferred to a fraudulent account. One remarkable new trend saw cybercriminals inviting company employees to a virtual meeting, then using a simulated audio deepfake of an executive’s voice to direct the employees to transfer the money.
The digital world is easy to manipulate, and in a healthy workplace setting, trust between coworkers is a pro, not a con. But the greatest weapon wielded against social engineering is critical thinking. If someone is requesting a wire transfer from you—why? Had they mentioned it prior? Does your relationship typically involve monetary transfers? It may be just to be safe, but will your boss please turn their camera on before you make the transaction?
It’s always best to follow up with email requests that seem out of the ordinary. If they’re legit, your colleagues will appreciate your devotion to keeping your virtual environment safe. If they’re not, you’ve just thwarted a cybercriminal who thought they could pull the wool over your eyes.
Get serious about cyber defense.
Mind Your Crypto
Another $1.46 billion in losses last year was funneled through investment scams, which have jumped in popularity in response to the rise of cryptocurrency. Crypto transactions made up an egregious number of successful cons, enabled in large part by crypto-compatible ATMs, which the FBI has criticized for poor regulation and their instantaneous, irreversible, high-risk transactions.
Interested in a seemingly golden investment opportunity? You’re best off doing your own research. If you want to form a partnership with an investor, think of it like the hiring process—you wouldn’t hire a candidate without a clean background check and solid references. As a general rule, people who contact you out of the blue or ask for something immediately are usually running a scam. Don’t hand them money; take the time to triple-check who you’re investing with.
Beware Your Heart
It’s one thing to be targeted by a seemingly legitimate investor or trusted colleague. But cybercriminals have range, and they know most people can’t resist a good tug at their heartstrings.
In 2021, fraudsters stole a whopping $956 million via confidence fraud and romance scams. In these truly personal attacks, a criminal adopts a false identity, usually seeking romance or companionship, and manipulates their victim’s emotions quickly and efficiently to convince them to share their account information or transfer money their way.
These cons are most common on dating sites and hit older individuals the most, but the dominance of social media in digital spaces has diffused them far and wide. The FBI notes that the scammers are uniquely skilled at building trust and endearing themselves to the victim, and although they may make grand promises and grander statements of love and devotion, they only like you for your bank account. They may also approach their victims purporting to be in desperate situations, seeking humanitarian aid for a recent crisis, or promoting a cause for charity.
When confidence fraud goes for the heart, use your head. Social media makes it easier than ever to search people’s names and photos and see if they’ve been used elsewhere. If your new contact asks you for money right away or personal contact information in favor of communicating via direct messaging, it’s likely the first step in phishing for more sensitive credentials. Ask lots of questions, and remember that if someone or their promises seem too good to be true, they probably are.
Build Social Smarts
Social engineering is and will remain a leading threat, and BAI Security offers serious countermeasures. BAI Security’s Social Engineering Evaluation is designed to turn your team into a human firewall, applying real-world methodologies specially engineered to put your employees against an authentic simulation and encourage a more security-conscious culture.
This service is an excellent complement to our Red Team Assessment, for a real-world test of your security defenses. We also offer a Vendor Management Risk Assessment, ensuring your Technology Service Providers (TSPs) are held to the same standards of risk management, security, and privacy your organization would be if you conducted your own in-house assessments.
Cybercriminals deploy their worst tactics against you—so hit back with IT security’s best, and contact us today.