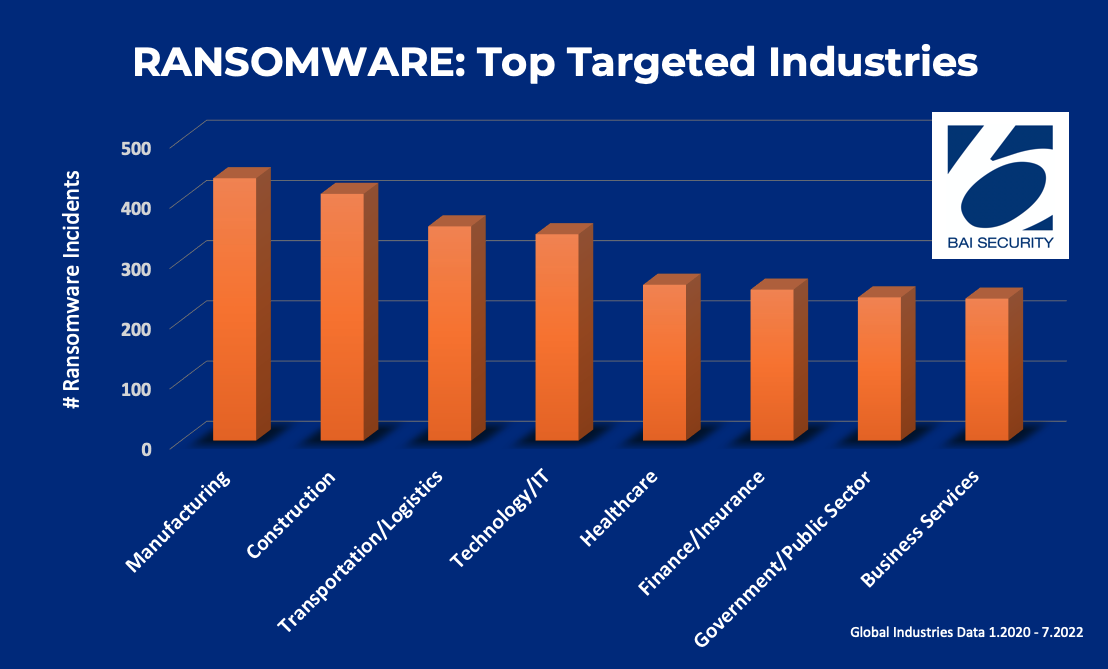
As the western world continues to lead in technology advancements, we see the same with a dark counterpart: ransomware attacks. A report spanning January 2020 to July 2022 indicates half of all globally recognized ransomware attacks aimed at the U.S., with 2,400 cases out of 5,200.
While healthcare has been a prolific target for malicious actors, especially over the course of the pandemic, hackers worldwide seem to be turning their attention to the Manufacturing industry, as well as Construction and Transportation/Logistics.
What are the common and attractive threads of these industries to cybercriminals?
First, complex supply chains.
The more links in the chain, the more potential points of entry by cybercriminals. As we’ve discussed previously in our articles about Validating Vendors and lessons from the SolarWinds breach, 60% of all data breaches will occur due to third-party issues.
Despite this fact, as well as frequent headlines highlighting breached supply chains, few organizations do much to confirm their partners’ security practices are. True validation of vendor security is a step CIOs are only now beginning to weigh, budget, and plan for. A future norm? We shall see and certainly hope for.
Get serious about cyber defense.
Secondly, lower risk—for the cybercriminal.
Contrary to frequent assumptions, hackers don’t always go where the reward is highest. They love to go where the risk is lower for them and where targets are less prepared. Compared to their larger counterparts, small- and medium-sized businesses (SMBs) have fewer resources allocated for cybersecurity and crisis response, making them exceptionally vulnerable to disruptive attacks.
In fact, evidence suggests ransomware attacks have little to do with the target’s size or revenue. SMBs suffered the most attacks in the two-year lookback. Entities that employed 11–50 and 51–200 employees made up 46% of affected organizations. Moreover, companies in the median revenue-wise actually had the highest annual instances of ransomware attacks.
Lessons From The Front Of The Line
The Manufacturing industry, which earned the ominous top spot on the ransomware targeted industries list, gets a double dose of risk. Manufacturers have complex supply chains loaded with vulnerability, AND the majority in the U.S. are SMBs with under 20 employees.
This isn’t the first time Manufacturing has been a favorite for targeted hacks. In 2020, 21% of ransomware attacks were against Manufacturing companies. The following year, a global study on the impact of ransomware found that about half of all victims in Manufacturing suffered lost revenue, and six in 10 reported struggling to keep up with their expanding attack surface.
Manufacturing faces a unique challenge, because they work with an Industrial Internet of Things (IIoT) linked to their Operational Technology (OT). Since OT tends to predate IIoT, rolling out remote updates can be difficult if not impossible. Hackers can target weak points in the IIoT to gain control of the OT and cause massive disruptions to operations. Malicious actors can gain further entry through complex supply chains, leveraging vulnerabilities in a supplier’s network to gain access to manufacturers and their customers.
There’s a lot to learn from entities with expansive scope like a manufacturer. The most effective structures designate separate OT and IT teams, with delegated responsibilities and strong lines of communication. Successful security strategies catalog and prioritize their assets, then use them to build a proportionate response when one is targeted. Ransomware relies on being able to confiscate data or functionality; therefore, knowing precisely what is in jeopardy and how to prevent spread is a key to damage mitigation.
In terms of supply chain, while it can be challenging to hold all your partners accountable, you can still do your part by vetting your vendors and challenging them to uphold your IT security standards. And in the case of an incident, communication remains key; the sooner a vendor can inform you of a breach, the faster you can brace for a potential attack.
You may also seek to collaborate with your partners on a disaster recovery plan. While 73% of surveyed entities in infrastructure reported having a written Incident Response Plan, only 21% noted an update in the last year. Recovery plans are an important part of normalizing a more cybersecure culture in the workplace, and they can give your employees a blueprint when they’re faced with a deliberately intimidating ransomware scenario.
Lastly, and as always, mandate soft- and hardware updates in a timely fashion. Be they remote or manual, nothing is worth the potential cost to your organization of falling behind on patches and other ongoing updates that could create an easy opening for cybercriminals.
Prepare, Prevent, Respond
Policies and plans are important, but real-world preparation has a distinct place in today’s defense strategies.
Our Ransomware and Endpoint Compromise Simulation poses a real-world endpoint compromise scenario against your organization. A facet of our comprehensive IT Security Assessment, this simulation will:
- Provide real-world testing in a fully controlled and RISK-FREE exercise
- Validate endpoint protection systems
- Determine the effectiveness of zero-day threat protection
- Assess the detection and alerts capabilities of your monitoring systems
- Evaluate the capabilities of your Incident Management Team
Stay ahead of cyberthreats—contact us today to get started!