Last month, a ransomware virus known as “WannaCry” made international headlines by infecting devices in more than 150 countries. In total, over 300,000 Windows-operating computers fell victim to this attack, forced to seek remediation by either being forced to pay a ransom to retrieve their data or relying on their previously backed-up data.
This was a unique attack. Oftentimes in this space, we discuss very targeted attacks on specific industries like healthcare and finance. The hackers perpetrating these more targeted campaigns do so for a reason – they’re counting on the element of surprise. They hope there won’t be news coverage of their attack, making it all the more easier to take advantage of the right IT infrastructure. Furthermore, financial and healthcare information is about as sensitive and valuable of information as you can get. With this data, there’s very little that these cyber-criminals can’t do when it comes to stealing identities and perpetrating fraud.
WannaCry did not stick to this playbook. Instead, this ransomware targeted thousands of organizations and users across the world with one thing in common – they all used Windows XP and other older versions of Windows as their operating systems (OS). We’re going to take you into the specifics of the WannaCry attack, sharing what you need to know and ways you can protect yourself from other future, yet likely similar, ransomware attacks.
Costly Infection
WannaCry functions relatively similar to other ransomware: it encrypts your files and demands payment via bitcoin in order to restore access to your data. News reports detailed that these attackers were demanding $300 in bitcoins to unencrypt these files; for reference, 1 bitcoin currently equals $1,768.18 USD. Not cheap.
Luckily, these attackers only managed to receive somewhere around $80,000 in bitcoins. While not an inconsiderable amount, for as widely spread as the attack was, you’d expect this figure to be higher. This is largely due to two factors; one, it was caught relatively early on and the virus’s kill switch was triggered, ending the initial attack; and two, the nature of the attack itself was limited due to the older versions of Windows it targeted which have stopped receiving Microsoft support in recent years.
Before we go much further, it should be noted that if you or anyone else in your organization is currently using an outdated Windows OS, you should download the Microsoft patch for this error right now. Furthermore, you should work with your IT staff or provider to update all of your PCs running an outdated OS. This is the only real fix to keep you safe from similar attacks in the future.
A Decade in the Making
WannaCry or “WannaCrypt” first popped up in 2001 as a bug on Windows XP. At some point after this, the Equation Group (the hacker collective allegedly connected to the NSA) came across the bug and possibly weaponized it. From there, a group known as the “Shadow Brokers” stole a set of NSA attack tools, including WannaCry, setting up our current predicament.
We’ve previously written about another malware threat the Shadow Brokers released known as “DoublePulsar,” so the WannaCry threat isn’t exactly unsurprising news. Security experts were aware threats like this were likely on the horizon, but the sheer amount of people targeted by this particular ransomware likely took many by surprise.
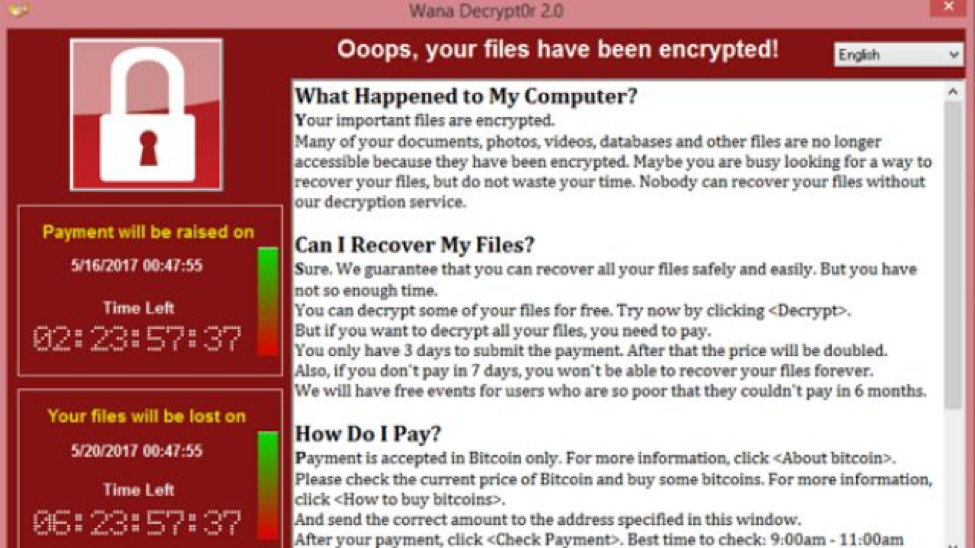
What it Looked Like
Users who were infected by WannaCry were presented with a screen that looked like this:
If you were to become infected by this or any other ransomware, you’re left with only a few options to remediate. One is to pay the ransom, which is obviously less than ideal. You could also use your (hopefully) frequently updated backup to restore your systems and face only minimal downtime. The final option is to employ recently released free decrypting tools, but in this scenario you’d want to move quickly, as the prime numbers stored in Windows memory which are used to build the crypto keys are eventually overwritten.
Whether or not you’ve been infected, you should update your computer to make sure your OS and other software is up-to-date, including any security patches that have been released. While this measure won’t protect you from all future ransomware attacks, it will greatly enhance your defense capabilities.
From there, you should take further precautions to keep your organization safe.
Our Solution
Along with frequent data backups that are stored offline, you need a virus and malware detection service that significantly lowers the odds your endpoints are infected by these viruses. Our Endpoint Protection / Next-Gen Antivirus service – powered by CylancePROTECT® – blocks WannaCry and other types of malware in real time using pre-execution artificial intelligence algorithms. This allows you or your IT service provider to take steps to remediate this threat – and avoid unnecessary downtime.
While the threat of this original strain of WannaCry has now been largely neutralized and contained, the menace of ransomware isn’t going anywhere. Hackers will – if they haven’t already – determine how to get around the security fixes put in place to stop it and unleash an updated virus. You need everything in your arsenal to push back against attacks like this.